Top Cybersecurity Threats
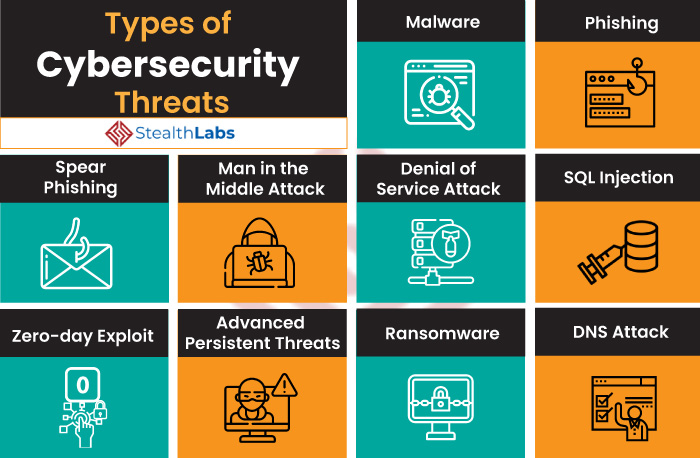
Exploring the realm of Top Cybersecurity Threats, this introduction aims to shed light on the critical challenges faced by individuals and organizations in the digital landscape. From common threats to emerging risks, this narrative delves into the ever-evolving world of cybersecurity with a focus on understanding, prevention, and protection.
Common Cybersecurity Threats: Top Cybersecurity Threats
Cybersecurity threats are a growing concern for individuals and organizations alike, as malicious actors continue to exploit vulnerabilities in systems and networks. Understanding the most common threats is crucial in order to protect sensitive data and prevent potential breaches.
1. Malware
Malware, short for malicious software, is a type of software designed to gain unauthorized access to systems or cause damage. Common types of malware include viruses, worms, Trojans, and ransomware.
2. Phishing
Phishing is a form of social engineering where attackers use deceptive emails or messages to trick individuals into revealing sensitive information, such as login credentials or financial details. These attacks often target employees within organizations.
3. Ransomware
Ransomware is a type of malware that encrypts files on a victim’s system and demands a ransom in exchange for decryption. This type of attack can have severe financial and operational consequences for businesses if not addressed promptly.
4. DDoS Attacks
Distributed Denial of Service (DDoS) attacks overwhelm a system or network with a flood of traffic, causing it to become slow or unavailable. These attacks can disrupt operations and lead to significant downtime for organizations.
Emerging Cybersecurity Threats

In today’s rapidly evolving digital landscape, new and emerging cybersecurity threats continue to pose challenges for organizations and individuals alike. These threats are gaining prominence and require proactive measures to mitigate the associated risks.
AI-Powered Attacks
AI-powered attacks are a growing concern as threat actors leverage artificial intelligence and machine learning algorithms to launch sophisticated and targeted cyber attacks. These attacks can bypass traditional security measures and adapt their strategies in real-time, making them difficult to detect and defend against.
Cryptojacking
Cryptojacking, the unauthorized use of a victim’s computing resources to mine cryptocurrencies, has become a prevalent threat in recent years. Cybercriminals exploit vulnerabilities in systems and devices to install mining scripts, leading to performance issues and increased energy consumption.
IoT Vulnerabilities
The increasing adoption of Internet of Things (IoT) devices has introduced new security challenges, as these connected devices often lack robust security features. Vulnerabilities in IoT devices can be exploited to launch large-scale attacks, compromising sensitive data and disrupting critical services.
Social Engineering Attacks
Social engineering attacks involve manipulating individuals to gain unauthorized access to sensitive information. These attacks exploit human psychology, tricking people into revealing confidential data or performing actions that compromise security.
Types of Social Engineering Attacks
- Pretexting: Involves creating a fake scenario to gain someone’s trust and extract information.
- Baiting: Tempts individuals with something desirable, such as a free download, to trick them into revealing personal details.
Exploiting Human Psychology
Social engineering attacks prey on common human traits like trust, fear, and curiosity. Attackers use psychological manipulation to deceive individuals and bypass security measures, ultimately gaining access to sensitive data.
Best Practices to Mitigate Risks
- Employee Training: Educate staff on recognizing social engineering tactics and the importance of verifying requests for information.
- Implement Multi-Factor Authentication: Add an extra layer of security to prevent unauthorized access even if credentials are compromised.
- Regular Security Audits: Conduct routine assessments to identify vulnerabilities and address them proactively.
Vulnerabilities in Cloud Computing

Cloud computing has revolutionized the way organizations store, manage, and access their data. However, along with its many benefits, cloud computing also introduces unique cybersecurity threats that organizations need to be aware of to secure their data effectively.
There are several vulnerabilities specific to cloud computing environments that organizations should be mindful of to prevent cyber attacks and data breaches. These vulnerabilities include misconfigured cloud storage, insecure APIs, and the risk of data breaches in the cloud.
Misconfigured Cloud Storage
Misconfigured cloud storage settings can leave sensitive data exposed to unauthorized access. Organizations must ensure that their cloud storage solutions are properly configured with the appropriate access controls and encryption protocols to prevent data leaks. Regular audits and security assessments can help identify and address any misconfigurations promptly.
Insecure APIs
Insecure APIs pose a significant risk in cloud computing environments as they can provide attackers with a gateway to access sensitive data stored in the cloud. Organizations should carefully review and secure their APIs to prevent unauthorized access and data breaches. Implementing strong authentication mechanisms and encryption protocols can help mitigate the risk of API vulnerabilities.
Data Breaches in the Cloud
Data breaches in the cloud can have severe consequences for organizations, including financial losses, reputational damage, and legal implications. It is crucial for organizations to implement robust security measures, such as encryption, access controls, and monitoring tools, to detect and respond to data breaches promptly. Regularly updating security patches and conducting security training for employees can also help prevent data breaches in the cloud.
Insider Threats
Insider threats refer to security risks that come from within an organization, involving current or former employees, contractors, or business partners who have access to sensitive data and systems. These threats can be either intentional or unintentional, posing significant risks to the organization’s cybersecurity.
Types of Insider Threats, Top Cybersecurity Threats
- Intentional Insider Threats: These are malicious actions taken by insiders with the intent to harm the organization, such as stealing confidential information, data breaches, or sabotage.
- Unintentional Insider Threats: These threats occur due to human error or negligence, such as falling victim to phishing attacks, clicking on malicious links, or inadvertently sharing sensitive information.
Impact of Insider Threats
Insider threats can have devastating consequences on an organization’s cybersecurity posture, leading to financial losses, reputational damage, regulatory fines, and loss of customer trust. These threats are often difficult to detect and can go undetected for a long time, causing significant harm.
Strategies to Mitigate Insider Threats
- Implement Strong Access Controls: Limit the access privileges of employees based on their roles and responsibilities to prevent unauthorized access to sensitive data.
- Conduct Regular Security Training: Educate employees on cybersecurity best practices, such as identifying phishing emails, using strong passwords, and reporting suspicious activities.
- Monitor User Behavior: Implement monitoring tools to track employees’ activities and detect any unusual behavior or unauthorized access to sensitive information.
- Establish Incident Response Plans: Develop a comprehensive incident response plan to respond quickly and effectively in case of an insider threat incident, minimizing the impact on the organization.
Essential FAQs
What are some common cybersecurity threats?
Common cybersecurity threats include malware, phishing, ransomware, and DDoS attacks, which exploit vulnerabilities in systems and networks.
What are emerging cybersecurity threats?
Emerging threats include AI-powered attacks, cryptojacking, and IoT vulnerabilities that pose new risks and challenges for cybersecurity.
How do social engineering attacks work?
Social engineering attacks manipulate human psychology to trick individuals into revealing sensitive information, such as through pretexting and baiting techniques.
What are insider threats?
Insider threats involve individuals within an organization who may intentionally or unintentionally compromise cybersecurity, highlighting the importance of detection and prevention strategies.